Electrum has long been one of the most popular Bitcoin software wallets. It’s fast, simple and lightweight. It’s a “light” wallet, that doesn’t require you to download a 150 gigabyte blockchain before you can do anything.
It turns out to have been completely insecure since 2015 — any web page you go to could have stolen your coins. If you use Electrum, get the latest version, 3.0.4, straight away. The update has also made it to Electron Cash and Electrum Litecoin.
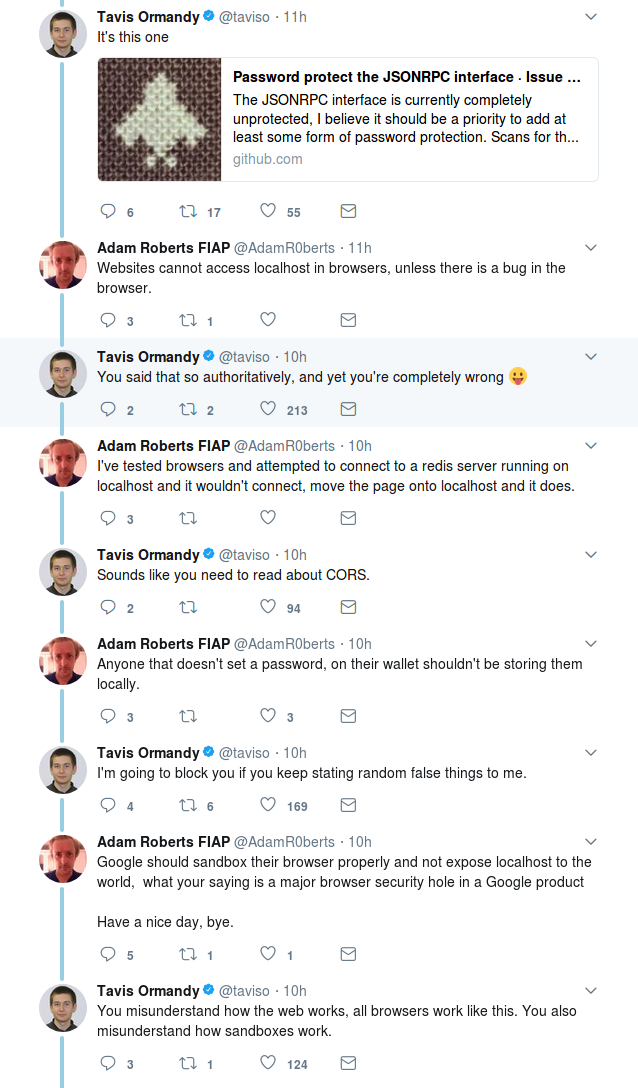
The problem is that the JSON RPC interface is completely open to anything else on your computer, e.g. a script running in your web browser — the software explicitly set a wide-open CORS policy.
Electrum didn’t just have a security hole — it was literally running an open server, for anyone to come in and take your money.
Tavis Ormandy is famous in computer security for his work at Google’s Project Zero initiative, finding unexpected and often quite creative security holes in common software and operating systems. He posted earlier today:
The bitcoin wallet Electrum allows any website to steal your bitcoins. I was gonna report it…but there was already an open issue from last year. I pointed out this is kinda critical, and they made a new release within a few hours. Update to 3.0.4 if you use it.
— Tavis Ormandy (@taviso) January 7, 2018
Ormandy had looked into it because “localhost RPC servers drive me crazy” — that is, applications that have a server running on your computer that accepts commands from software running locally.
I installed Electrum to look, and I’m confused why this isn’t being treated as a critical and urgent vulnerability? If this bug wasn’t already open for months, I would have reported this as a vulnerability, but maybe I misunderstand something.
The JSON RPC server is enabled by default, it does use a random port but a website can simply scan for the right port in seconds.
I made you a demo. It’s very basic, but you get the idea.
If you did set a password, some misdirection is required, but it’s still game over, no?
The code implementing this dates back to the original implementation of the JSON RPC interface in August 2015. This hole has been open since then.
Although the problem had first been raised in November last year, Ormandy’s proof-of-concept was clear enough to get the project scrambling. A fix was committed and a new version released within hours.
The Electrum JSON RPC interface still doesn’t have password protection, though this is currently being implemented. But at least a random web page can’t clean out your wallet now.
Bitcoin users responded to news of the security hole as you might expect, including accusing Ormandy of not understanding computer security:
The replies you get when you say the word "bitcoin" 😆 https://t.co/JirhS7A9An
— Tavis Ormandy (@taviso) January 7, 2018
Electrum users have been reporting unexplained hacks for the last couple of years. The usual response from the community is victim-blaming.
It’s likely this problem was already known to the bad guys. Bleeping Computer reported last November about massive scans for Ethereum wallets. That security hole isn’t this one — Ethereum doesn’t use the Electrum wallet software — but that too accessed the Ethereum software’s JSON RPC interface. Making a financial application into a server is dangerous and tricky.
The more general problem is that cryptocurrency security is vastly harder than any normal user can be expected to achieve — because every mistake or theft is utterly irreversible, by design. As I note in chapter 3 of the book:
“Secured by math” means the cryptography is strong – but it says nothing about everything else you need to use bitcoins safely in practice. “Be your own bank” means you take on the job of providing all the security and technical knowledge that a regulated professional institution normally would.
The Bitcoin Wiki offers a page with step-by-step instructions on how to secure your personal Bitcoin wallet that would dismay even a typical IT professional, let alone a casual computer user. You will need a security specialist’s understanding of the possible modes of attack on a modern operating system, how to encrypt all data securely and yet accessibly, password strength, backup procedures, how to securely erase a disk, the quirks of whatever Bitcoin wallet software you’re using …
(The linked Bitcoin Wiki page has been considerably simplified since the book’s release. The issues listed don’t go away, however.)
Users download software from Github because they read on a forum that it was okay, and then they just assume that someone else has done the security legwork, and there are no holes. (Or keyloggers.)
The alternatives aren’t much better. When someone’s software wallet gets hacked, the usual response from advocates is “use a hardware wallet!” Then you’re trusting the vendor didn’t use insecure hardware. Or that the vendor didn’t sell you a wallet with a key that they know:
WARNING: Brutal scam. Guy buys a Ledger Nano wallet on Ebay, and it steals all his cryptocurrency ($34,000, which is his life's savings). • r/btc https://t.co/nePcqGJYiu pic.twitter.com/yGjZLBysvy
— Andrew Jackson (@realOldHickory1) January 6, 2018
Or people could use conventional currency via a card linked to an account at an insured and regulated bank, who pay expert professionals to do this stuff. With laws that ensure your money is protected.
Irreversibility all the way through the system is bad and stupid. Pervasive irreversibility is the root cause of pretty much every problem in cryptocurrency.
https://twitter.com/austinzheng/status/949848258683138048
Your subscriptions keep this site going. Sign up today!


Irreversibility happens to also be a main feature, aka “the whole point”. Nice troll though.
^^ teetering on the brink of epiphany
So close to understanding the problem and yet so far…