A “smart contract” is a computer program running right there on the blockchain itself, so you can do complicated things with your cryptocurrencies and tokens, automatically. Ethereum was the first popular smart contract platform.
Smart contract programs are extremely hard to alter — in Nick Szabo’s original conception of the idea, they were impossible to alter.
The idea is that you can have faith that the program is immune to interference from mere humans — that you’ve automated the human element out.
The problem there is that another term for “immutable program” is “sitting duck for attackers.”
The root cause of smart contract issues in practice is the clash of two factors:
- Smart contracts are hard or impossible to alter, by design. They require the most painstaking code review and analysis — so that you don’t lose money to an exploit.
- You make more money by being quick to market.
Decentralised Finance, or DeFi, uses chains of smart contract programs to automate complex financial transactions — so you can chain the attacks too. Unsurprisingly, it’s a continuing dumpster fire, reliably delivering comedy gold.
dForce pulls a DAO
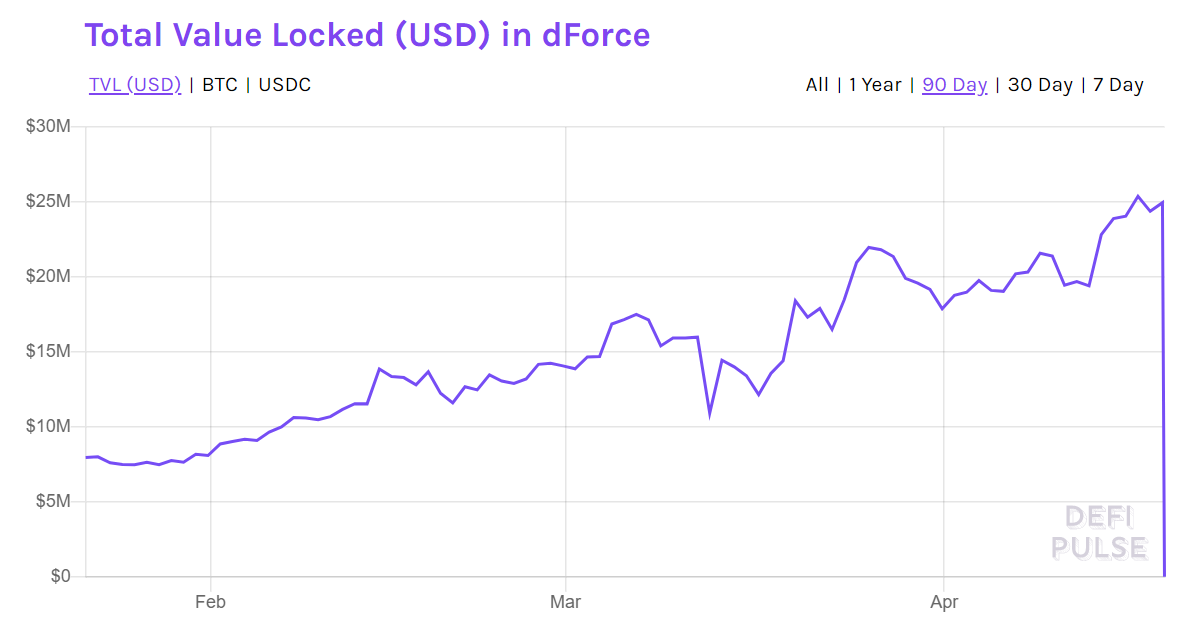
DeFi provider dForce suffered an unfortunate exploit of its lendf.me protocol on 18 April — in which an attacker took off with $25 million of assets under management, leaving just $18,900. [CoinDesk]
The assets were mostly ether and bitcoins — not actual ether and bitcoins, but tokens representing them. The exploit involved using imBTC tokens as collateral.
imBTC is an ERC-777 token. ERC-777 is an updated version of the ERC-20 standard, which most ICO token contracts were built on — but the imBTC smart contract had a re-entrancy bug, where you could withdraw repeatedly before the balance updated. (This is the sort of bug The DAO fell to in 2016.)
After sufficient iterations, the attacker used their imBTC balance as collateral to borrow multiple other assets. The attacker then surrendered their collateral, and kept the borrowed assets. [Twitter]
The imBTC pool on Uniswap had been attacked and drained the same way, the previous day. [Twitter]
Peckshield wrote up both attacks. “ERC777 itself is a community-established token standard with its advanced features for various scenarios. However, these advanced features might not be compatible with certain DeFi scenarios. Worse, such incompatibility could further lead to undesirable consequences (e.g., reentrancy).” [Medium]
The attacker returned some assets to dForce — tokens they couldn’t possibly cash in, because the tokens were centrally issued, and were already blacklisted by the issuer. These included Huobi BTC and Huobi USD, two ERC-20 tokens representing bitcoins or US dollars, that can only be redeemed at the Huobi crypto exchange. [Twitter]
DeFi startup Compound alleged a few months ago that dForce had copied its code — the word “compound” appears throughout dForce’s code. Compound’s code is not under an open source copyright license — it’s all-rights-reserved, with the source being publicly available. [The Block, paywalled; GitHub; GitHub]
Hegic Options — security theatre as a service
Hegic is an on-chain options trading protocol on Ethereum — intended for use in decentralised finance (DeFi). Hegic proudly proclaims it was audited by Trail of Bits, before its launch on 24 April. [Hegic]
The next day, Hegic alerted users to a bug in the code: “!! ALERT A typo has been found in the code. Because of that, liquidity in expired options contracts can’t be unlocked for new options. ‼️ Please EXERCISE ALL OF YOUR ACTIVE OPTIONS CONTRACTS NOW.” [Twitter]
The bug was a typographical error in a function name — Hegic used options.length instead of optionIDs.length, while they had options defined in outer scope, so the Solidity compiler tried to use that. [Twitter; GitHub]
Hegic originally reported the bug incorrectly: “It’s an incorrect function name (optionIDs instead of optionsIDs).” But they did describe the consensequences correctly: “This function unlocks liquidity in expired contracts. If it doesn’t work, funds are just forever locked.” In any case, Hegic will be refunding any funds that were locked by the bug. [Twitter]
Trail of Bits was not so happy that Hegic claimed they had “audited” the smart contract. CEO Dan Guido asked them in a tweet: “Please stop holding up a 3-day code review as an ‘audit’ that proves the code is safe.”
Guido later deleted that tweet, but he did post a thread explaining precisely what Trail of Bits had — and hadn’t — done: [Twitter]
In 3 days earlier this month, we identified 10 critical flaws in @HegicOptions that could harm users. We noted a lack of tests, a lack of documentation, and that the time afforded to review their code was insufficient.
Bottom line: we told them to hold off deploying. This was the right advice, and we generally expect people listen to us when they’re paying for our help.
Instead, Hegic patched the few bugs we found, made no further changes, misrepresented our 3-day code review as an “audit”, then immediately deployed.
Trail of Bits has fired Hegic as a client. [Twitter]
The audit summary itself is a collection of polite ways to phrase “this program is laughably ill-constructed and has so many problems we didn’t have time to find them all.” MyCrypto summarised Trail of Bits’ audit summary in a Twitter thread. [Trail of Bits, PDF; Twitter]
This will keep happening
I published “Smart contracts, stupid humans”, chapter 10 of Attack of the 50 Foot Blockchain, in 2017 — which I foolishly thought would knock this deeply and fundamentally dumb and bad idea on the head. If you don’t have the book, I did an interview a few months later, about why smart contracts are fundamentally dumb and bad, that covers some of the same ground.
The problem with DeFi is not the technology, though that’s bad too — it’s that people are greedy and foolish.
Update: corrected the Hegic bug description — Hegic misdescribed their own bug, just as if they didn’t know the code very well. (Cheers to myfreeweb on lobste.rs.)
Your subscriptions keep this site going. Sign up today!